How does the BDSLCCI Framework's Defense in Depth (DiD) contribute to the distribution of PREVENTIVE, DETECTIVE, DETERRENT, RECOVERY, and CORRECTIVE Control Areas?
February 21, 2024 | Revised January 1, 2025
The Business Domain Specific Least Cybersecurity Controls Implementation (BDSLCCI) Framework is complying with the maximum cybersecurity control areas in defense in depth (DiD), which are helpful for micro, small, and medium enterprises known as SMEs, SMBs, MSMEs, or startup companies.
This article will help you understand different control types and cybersecurity areas, along with how the BDSLCCI cybersecurity framework will provide wide coverage of those.
In cybersecurity, implementation controls are mainly divided into the below five categories.
- Preventive Controls: Helps to avoid any incident from occurring.
- Detective Controls: Finds information and specifics related to the actions of an occurrence.
- Deterrent Controls: A strategy or measure to deter a possible miscreant.
- Recovery Controls: Controls put in place to rapidly return the environment to normal functioning.
- Corrective Controls: Fixes systems or components following an incident.
Again, these controls have many different dimensions contributing to administrative, physical, technical (logical), and a few other areas.
The below table shows coverage of Defense in Depth (DiD) cybersecurity controls in align with BDSLCCI Framework. In this table, "Green" color with "Y" indicates the applicability of a control to a particular type of control.
| BDSLCCI DiD Level |
List of Security CONTROLS |
PREVENTIVE |
DETECTIVE |
DETERRENT |
RECOVERY |
CORRECTIVE |
BDSLCCI
DiD
Level-1 |
1.1 - Host/Endpoint - Less Permission to Use
|
Y
|
Y
|
Y
|
|
|
| 1.2 - Host/Endpoint - Endpoint Protection - Anti-Virus
|
Y
|
Y
|
|
|
Y
|
| 1.3 - Host/Endpoint - Licensed Operating System (OS)
|
Y
|
|
|
Y |
|
| 1.4 - Host/Endpoint - Block File Transfers
|
Y
|
Y
|
Y |
|
|
| 1.5 - Data - Encryption
|
Y
|
|
|
|
|
| 1.6 - Data - Access control
|
Y
|
Y
|
Y |
|
|
| 1.7 - Data - Backup
|
Y
|
|
|
Y |
Y |
| 1.8 - Data - Data Loss Prevention
|
Y
|
|
|
Y |
|
| 1.9 - Data - Secure Deletion
|
Y
|
|
Y |
Y |
Y |
| 1.10 - Human - Cybersecurity Awareness Training
|
Y
|
|
Y |
|
|
| 1.11 - Human - Separation of Duties
|
Y
|
|
Y |
|
Y |
| 1.12 - Human - Service Level Agreement (SLA)
|
Y
|
|
Y |
|
Y |
| 1.13 - Human - Employee Background Check
|
Y
|
Y |
Y |
|
|
| 1.14 - Human - Review Access Rights
|
Y
|
Y |
Y |
|
Y |
| 1.15 - Human - Cyber Threat Alert Notifications
|
Y
|
|
Y |
|
Y |
| 1.16 - Human - Cybersecurity Banners / Posters
|
Y
|
|
Y |
|
|
| 1.17 - Human - Non Disclosure Agreement (NDA)
|
Y
|
|
Y |
|
|
BDSLCCI
DiD
Level-2 |
2.1 - Network - Network Firewall
|
Y
|
Y
|
|
|
Y |
| 2.2 - Network - Network Access Control
|
Y
|
Y
|
Y |
|
|
| 2.3 - Network - Remote Access VPN
|
Y
|
|
|
|
|
| 2.4 - Network - Instruction Detection & Prevention Systems (IDPS)
|
Y
|
Y
|
Y |
|
Y |
| 2.5 - Application - OWASP Coding Practices
|
Y
|
Y |
|
|
Y |
| 2.6 - Application - Application Hardening
|
Y
|
Y
|
|
|
Y |
BDSLCCI
DiD
Level-3 |
3.1 - Physical Perimeter - Locked and Dead-Bolted Steel Doors
|
Y
|
Y
|
Y
|
|
|
| 3.2 - Physical Perimeter - Closed-Circuit Surveillance Cameras (CCTV)
|
Y
|
Y
|
Y |
|
|
| 3.3 - Physical Perimeter - Picture IDs
|
Y
|
Y |
Y |
|
|
| 3.4 - Physical Perimeter - Security Guards / Proper Lighting / Biometrics / Environmental Control
|
Y
|
Y
|
Y |
|
|
| 3.5 - Governance - Incident Response Process
|
|
|
Y |
Y |
Y |
| 3.6 - Governance – Business Continuity Plan (BCP)
|
|
|
Y |
Y |
Y |
| 3.7 - Governance - Periodic Audit
|
Y
|
Y |
Y |
|
Y |
Let's understand more about these categories of cybersecurity controls.
PREVENTIVE Controls:
A cybersecurity measure implemented with the goal of averting an incident is known as a preventative measure. Preventive control aims to avert problems before they arise. The idea behind preventive control is to try and stop any unauthorized efforts to alter a system before they happen. If successful, this should theoretically mean that an attack won't succeed. An example of a stopped attack would be if a malevolent actor tried to compromise a host's online account, but the host was not online. Preventive controls are usually implemented in the form of non-overridable methods. Because they are methods that are supposed to be applied correctly and cannot be changed, a malicious actor cannot circumvent them by altering them.
Preventive mechanisms and controls lengthen the time required to complete specific system tasks and are frequently process-oriented. Preventive controls may have the unintended effect of making regular system use more difficult. In these situations, the management of the company should decide whether or not preventive controls are the appropriate control functionality option to be adopted.
DETECTIVE Controls:
Developing detective controls is essential to constructing cyber resilience.
By making harmful activities and possible intrusions into IT infrastructure more visible, detective controls enable the right team members to be promptly notified in the case of an attack. These controls also aid in raising the standard of the reaction given after a security incident.
DETERRENT Controls:
Threats are deterred from trying to take advantage of a vulnerability by deterrents.
These controls assist companies in deterring their staff members from purposefully triggering a security breach. Many times, it works through the denial principle, which aids deterrence. It is covered to the to the maximum via physical and administrative controls.
RECOVERY Controls:
For any unseen or unpredicted event, organizations need to prepare with recovery planning. These controls help in this crucial area.
This recovery of a business's critical assets, such as a database, should be done in a secure manner without compromising cybersecurity needs. That is the main objective of recovery controls.
CORRECTIVE Controls:
Corrective controls are actions done after an undesirable or illegal activity to fix harm or return resources and capabilities to their original state.
In the context of cybersecurity, corrective controls, also known as correction controls, are essential procedures and methods used to address any weak points in the computer and data infrastructure. Typically, these controls are created and implemented in order to address anomalies after they have had an impact on the system.
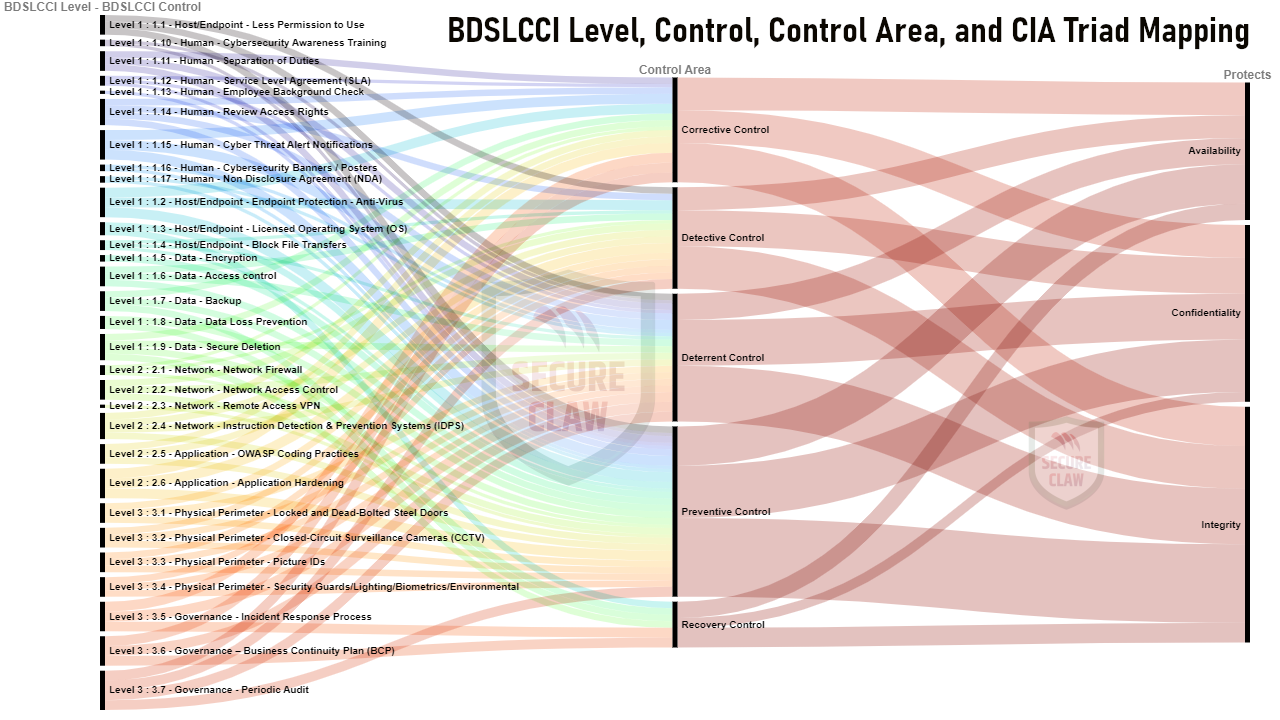
The below diagram indicates how confidentiality, integrity, and availability (CIA triad) are mapped with these control areas in BDSLCCI levels.
Cybersecurity is right for every business, regardless of its size, location, or revenue! The BDSLCCI Cybersecurity Framework complies with the maximum cybersecurity controls's categories using a tailored list of controls, especially useful for micro, small, and medium enterprises known as SMEs, SMBs, MSMEs, or startup companies.
by Dr. Shekhar Ashok Pawar
Visit www.BDSLCCI.com today to know more features and benefits!
Latest BDSLCCI framework 3.0 has modified Defense in Depth (DiD) as well as Mission Critical Asset (MCA).
OVERVIEW of BDLSCCI Framework:
SecureClaw Incorporation is the second venture of Dr. Pawar, which is on the mission of cybersecuring small and medium companies worldwide, which are known as MSMEs, small and medium businesses (SMBs), or even small and medium enterprises (SMEs), depending on their size, revenue, and location. For this article, let us consider the word SMB, which represents any of these kinds of companies. With his decades of international experience and research studies during his doctorate from the Swiss School of Business and Management in Geneva, Switzerland, Dr. Pawar has invented a new cybersecurity framework popularly known as Business Domain Specific Least Cybersecurity Controls Implementation (BDSLCCI), which is more focused on these kinds of organizations. Apart from continuous research and enhancement in BDSLCCI to make it more beneficial to MSMEs, SecureClaw also provides various cybersecurity services, which include the Virtual Chief Information Security Officer (V-CISO), Source Code Security Review, which is popularly known as static application security testing (SAST), dynamic application security testing (DAST), or vulnerability assessment and penetration testing (VAPT), as a few of its key offerings. These organizations have diverse experience in programming, telecom, and cybersecurity, which makes their expertise unique while designing solutions for their customers.
During international research studies by Dr. Pawar, the top management of SMB companies from 19 different countries participated.
It was evident that there were three major problems faced by those companies.
- Small and medium-sized companies are not having enough funds or allocated budget for the implementation of hundreds of controls mandated by existing cybersecurity standards.
- These companies do not have skilled teammates or other resources to implement and maintain cybersecurity controls.
- Top management is not able to see the return on investment (RoI) for cybersecurity implementation, as the top priorities of such companies are not directly aligned with the recommended controls by existing cybersecurity standards or frameworks.
Dr. Pawar's research reveals that each SMB has a unique business domain and mission-critical asset (MCA) based on their sector. MCAs, such as data, information, or infrastructure, are crucial for a SMB's core business. For instance, healthcare MCAs might be Electronic Medical Record (EMR) software, while banking, financial services, and insurance (BSFI) MCAs might be financial records. MCAs can be information-related or even business function-related.
MCAs weigh confidentiality, integrity, and availability differently, and SMBs need cybersecurity controls. Defense in Depth (DiD) strategy addresses people, process, and technology. BDSLCCI framework provides recommendations for implementing DiD controls in parallel with MCA, designed by Dr. Pawar.
There are multiple ways to get BDSLCCI certification.
- SMB can self-assist by directly registering itself on the BDSLCCI web portal. The BDSLCCI web portal provides secured access to various data points and guidance provided by the logic of the BDSLCCI framework.
- SMB can identify a BDSLCCI member company, which is a certification body of BDSLCCI, authorized to provide BDSLCCI certificates as one of its services.
- SMB can even hire BDSLCCI-authorized freelancers who can assist them in their BDSLCCI certification journey, where the final audit will be done by SecureClaw and the BDSLCCI certification and transcript will be issued by SecureClaw.
The BDSLCCI offers certifications and assessments at three different levels. On the incremental order of control implementation, SMB can be more cybersecure while reaching BDSLCCI Level 3.
BDSLCCI 3.0 has been available since January 2025 with modified cybersecurity control areas and a more prioritized approach to protect against the latest cyber threats.
Any startup, even one employee company, or any medium-scale company with hundreds of employees can get a customized or tailored cybersecurity controls list using BDSLCCI. It offers an ascending order of controls, aiding top management in decision-making. In situations where organizations need to take the Data Privacy and Protection Acts of their nation seriously to avoid high penalties if a data breach happens, or even to avail of cyber insurance, or to simply have better confidence in their way of working and handling customers’ critical assets, selecting SecureClaw’s BDSLCCI will be a very good choice. SecureClaw has been deployed in many SMBs/ SMEs/ MSMEs and has received good market feedback.