How BDSLCCI Cybersecurity Framework can help organizations to adopt DIGITAL PERSONAL DATA PROTECTION (DPDP) requirement?
The Digital Personal Data Protection (DPDP) Bill, which aims to protect citizens' privacy, was approved by voice vote in the Lok Sabha on August 7, 2023. The Ministry of Electronics and Information Technology published a draft of the law in December 2022 and requested public feedback on it (2022 Draft). The Information Technology Act of 2000 (IT Act) and the provisions of the Right to Information Act of 2005 are two laws that the DPDP Bill seeks to change and delete once it becomes law.
The goal of the Digital Personal Data Protection (DPDP) Bill 2023 is to safeguard and protect people's private information. It establishes a unique organization called the Data Protection Board (DPB) to deal with issues including improper data use. Companies now have to designate a Data Protection Officer (DPO) and provide users with contact information. The law also gives the government the power to decide when to send personal data abroad. Companies may be penalised between Rs 50 crore and Rs 250 crore for breaking the guidelines. Data exposure has occurred in some instances, like as when information of SBI bank workers was posted online.
BDSLCCI cybersecurity framework can help organizations to adopt requirement of the Digital Personal Data Protection (DPDP) Bill, 2023 of India.
by Dr. Shekhar Pawar
The DPDP Bill's reach on the legislative front:
- Even if the data is held on the computers of other businesses, the companies that utilize or deal with the data of people must ensure its security.
- The business is required to notify the Data Protection Board (DPB) and the individuals impacted if there is a concern with data being used improperly.
- Only with the consent of the children and/or individuals with disabilities can information about them be used.
- People should be able to contact the designated individual at each company, who is known as the data protection officer (DPO).
- A corporation may be fined if it violates the guidelines or utilizes customer information improperly. The penalty might range from INR 50 crore and INR 250 crore.
Important features of the Digital Personal Data Protection (DPDP):
Every organization and individual in India must understand the importance of DPDP. In below sections, the DPDP's scope will be examined, the applicable parties will be clarified, and key terminology, clauses, and exemptions will be covered in greater detail.
PENALTIES FOR NON-COMPLIANCE:
If the Data Protection Board determines a data fiduciary has violated the DPDP, they may impose a monetary penalty for each violation committed. The exact penalty a data fiduciary may receive will be determined by the DPDP official schedule and by the board based on the following factors:
-
The nature, gravity, and duration of the breach
-
The type of personal data affected by the breach
-
Repetitive nature of the breach
-
Gains or loss avoidance achieved through the breach
-
Acts taken to mitigate the impact or consequences of the breach
-
According to the official DPDP schedule, data fiduciaries who experience a data breach after failing to install security safeguards will encounter the most severe penalties, extending to a maximum of 250 crore (2500 millions) rupees.
PERSON:
Any of: (i) an individual; (ii) a Hindu undivided family; (iii) a company; (iv) a firm; (v) an association of persons or a body of individuals, whether incorporated or not; (vi) the State; and (vii) every artificial juristic person, not falling within any of the preceding sub-clauses.
PERSONAL DATA:
Any data that relates to or allows for the identification of a certain person. The DPDP Bill designates some personal information as sensitive personal information. This includes any type of information the government specifies after consulting with the Authority and the relevant sectoral regulator, such as -
-
Name of person
-
Address of person
-
Phone number of person
-
Email address of person
-
Financial data of person
-
Biometric data of person
-
Caste, religious or political opinions of person
-
or any other category of information.
PERSONAL DATA BREACH:
Any unauthorised processing of personal data or accidental disclosure, acquisition, sharing, use, alteration, destruction or loss of access to personal data, that compromises the confidentiality, integrity or availability of personal data.
DATA PRINCIPALS:
Refers to the individual whose data is being collected. The parent or legal guardian of the person to whom the personal data belongs when that person is a child (who are less than 18 years of age) or a person with disability is also considered to be that person.
PERSONAL DATA PROCESSING:
A fully or partially automated operation or set of operations performed on digital personal data. These operations include gathering, organizing, structuring, storing, adapting, retrieving, using, aligning, or combining, indexing, sharing, disclosing by transmission, disseminating, or otherwise making available, restricting, erasing, or destroying.
DATA FIDUCIATIES:
Any person who alone or in conjunction with other persons determines the purpose and means of processing of personal data. Data controllers and other entities that choose the use of a data principal's personal information are considered data fiduciaries. Startups and organizations collaborating with processors or other third-party service providers that retain or utilize personal data are included in this definition.
SIGNIFICANCE OF DATA FIDUCIATIES:
The DPDP was also used by the Indian Central Government to define a new class of data fiduciaries. Significant data fiduciaries are determined by the government based on evaluations of pertinent variables like:
-
The volume and sensitivity of personal data
-
Risk to the rights of a data principal
-
Potential impact on the sovereignty and integrity of India
-
Risk to electoral democracy
-
Security of the territory of India
-
Public order
After the Central government classifies a fiduciary as a significant data fiduciary, the data processor must complete additional obligations and appoint a data protection officer.
APPLICATION:
Applies to personal data that is processed in connection with any activity involving providing goods or services to data principals inside India, including data acquired (i) online, (ii) offline but later converted to digital form, and (iii) outside India.
It is not appled to - (i) personal data processed by an individual for any personal or domestic purpose (like keeping an own phone book with your name, number, etc.); and (ii) personal data that is made or caused to be made publicly available by - (A) the Data Principal to whom such personal data relates (Disclosure through an individual blog, videos, social media, etc.); or (B) any other person who is under an obligation under any law for the time being in force in India to make such personal data publicly available.
COUNTRIES TO WHICH CROSSBORDER PERSONAL DATA TRANSFER ALLOWED:
Unless the Central Government of India specifies differently, all nations and territories.
EXPLICIT CONSENT:
Data principals must receive a notice in plain and understandable language that outlines the personal information that will be collected, why it is being collected, how data principals can exercise their right to withdraw consent and file a grievance, and how to complain to the Data Protection Board (DPB).
BREACH REPORTING:
Unlike the 2022 Draft, only data fiduciaries are responsible for disclosing breaches and are held liable for failure to do so. In the event of a personal data breach, the Data Fiduciary shall give the Board and each affected Data Principal, intimation of such breach in such form and manner as may be prescribed.
What Rights Does the DPDP Grant to Data Principals?
In order to stop breaches of personal data and give all relevant data principals access to data privacy, the Indian government passed the DPDP. Data principals are granted the following fundamental rights under the act:
-
RIGHT TO BE FORGETTEN:
Mandates that data processors cease processing personal data on withdrawal of consent. Additionally, once the retention of the personal data is no longer necessary for compliance with any law, the data processor must erase any such personal data.
-
RIGHT TO DATA PRINCIPALS:
The Data Principal shall have the right to access, consent, erase, and nominate reference to its information.
-
RIGHT TO DATA NOMINATE:
Designate a person to represent your interests in the case of your death or incapacitance. However, the government will announce the precise procedure when it is appropriate.
In more elloborative way, DPDP act is covering below rights:
-
The right to give consent for the processing of personal data
-
The right to withdraw consent for the processing of personal data
-
The right to access information about personal data
-
The right to erasure and the right to correct, update, and complete personal data
-
The right to readily available grievance redressal in the event a data fiduciary fails to carry out their obligations under the act
-
The right to nominate any other individual to carry out their data principal rights in the event of death or incapacity
APPOINTED DATA PROTECTION OFFICERS:
Significant data fiduciary is required to comply with additional obligations such as appointment of a data protection officer residing in India, appointment of an independent data auditor, undertake data protection impact assessments and ensure compliance with other measures as may be prescribed.
Exemptions: In below cases it is possible to get exemption.
-
The government has the authority to inform specific data fiduciaries—which may include numerous DPIIT-registered startups—that particular DPDP regulations might not apply to them. The quantity and type of personal data processed by such notified companies may serve as the primary basis for such exemptions.
-
If it's required for research, archiving, or statistical purposes and the personal data won't be used to make decisions that are unique to a Digital Nagarik, the government may also be excluded in some situations.
The BDSLCCI cybersecurity framework not only protects mission-critical assets of the organizations but also provides step-wise defense-in-depth control deployment, which has a data security layer at the heart of the implementation and can be mapped with the DIGITAL PERSONAL DATA PROTECTION (DPDP) requirement.
Cyber resilience is a concept that combines organizational resilience, cyber space security, and business continuity. In other words, the idea refers to the capacity to carry on achieving desired results in the face of difficult cyber events like cyberattacks, natural catastrophes, or economic downturns.
The below diagram shows how BDSLCCI's Defense in Depth (DiD) can protect personal data present within the organization, considering it one of its mission-critical assets (MCA).
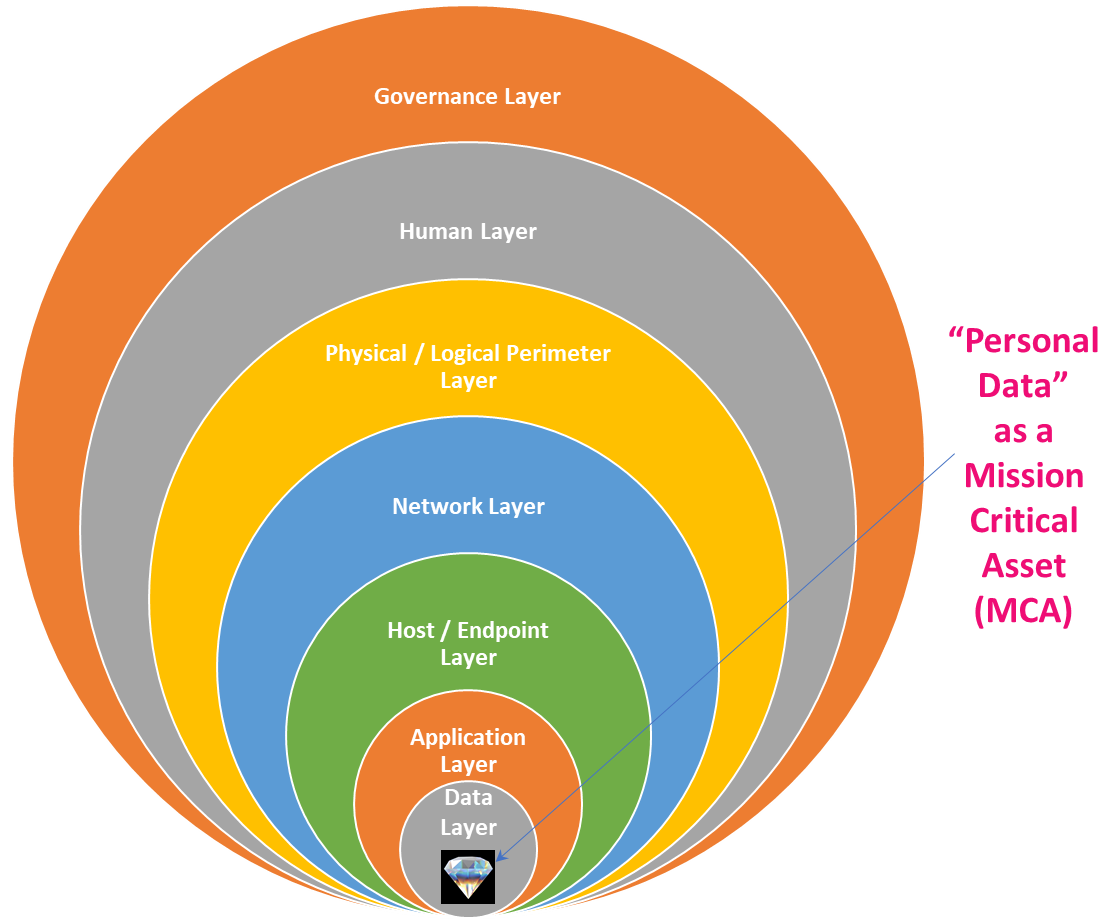
According to the latest research published in 2022, "LCCI: A Framework for Least Cybersecurity Controls to be Implemented for Small and Medium Enterprises (SMEs)" in Elsevier’s JJIMEI international journal, one out of every two SMEs is facing a cyberattack. It costs more than $2.2 million a year on average; 43% of cyberattacks target small businesses; and 60% of small businesses shut down within six months of a cyberattack. According to Dr. Shekhar Pawar, hackers are developing new methods to improve their ability to commit cybercrime. "An earlier ransomware attack was only encrypting the computers, and asking for a ransom for the decryption key,” says Dr. Shekhar Pawar. "Following the decryption key ransom, cybercriminals began threatening victim organizations with selling the hacked data on the dark web. It is double extortion. Now, recent cyber news is talking about triple extortion, where hackers can further use the hacked information to perform a Distributed Denial of Service (DDoS) attack to flood the victim's server with traffic, etc.”
Dr. Shekhar Pawar, founder and CEO of SecureClaw Inc, USA, having diverse international work experience in cybersecurity, software development, and teleservices, took the initiative to dig into the root cause of the problem faced by the top management of the SME while implementing cybersecurity controls. He had conducted an analysis of the various inputs from the top management of SME companies in 19 countries during his doctoral studies on the cybersecurity of the SME segment at SSBM Geneva, Switzerland. The participating SMEs were from Australia, Bangladesh, Cyprus, Ghana, Hong Kong, India, Indonesia, Israel, Malaysia, Nigeria, Norway, Russia, Singapore, South Africa, Sri Lanka, Sweden, the United Arab Emirates, the United Kingdom, and the United States. According to research, existing leading cybersecurity standards appear very expensive for SMEs, as they demand hundreds of controls to be implemented. Also, SMEs do not have enough resources to adequately implement those. More importantly, existing standards are providing a common, generic set of cybersecurity controls for all the business domains, where top management can’t see relevance to their business priorities and ROI. It has caused many SMEs to either not go ahead with the cybersecurity controls implementation or to choose any random controls as their own.
As an outcome of the international research studies, Dr. Shekhar Pawar has invented and published internationally “Business Domain Specific Least Cybersecurity Controls Implementation (BDSLCCI)” which provides tailored cybersecurity controls for each business domain of the SME segment, reducing the number of controls to be implemented, the required time, and the overall implementation cost, and hence increasing the return on cybersecurity implementation investment (ROI). Via BDSLCCI logic, it possible to identify a set of cybersecurity controls for a particular SME depending on its business domain requirements. It means that SME working in e-commerce must implement certain controls, while SME working in manufacturing must implement their own set of cybersecurity controls, and so on. There are three stages of the BDSLCCI journey of SME, known as Level 1 through Level 3. It helps the top management of SME businesses to invest stage-wise with direct protection for the mission-critical assets of their business. SecureClaw Inc. has developed BDSLCCI.com, an AI and machine learning-based web platform. Any SME representative can sign up by visiting a web portal and utilizing its user-friendly functionality.
When a SME representative logs in to the BDSLCCI web portal, an AI-ML based software algorithm shows the recommended stage-wise cybersecurity control journey. SME can implement those, upload evidence showing effective implementation, and get a certificate of the BDSLCCI level attained after an online audit performed by the BDSLCCI auditors.
Additionally, SecureClaw is developing simple-to-use cybersecurity tools for small and medium-sized businesses to help them stay one step ahead of online threats.
BDSLCCI is expanding its network of certified lead auditors and member organisations worldwide, which will provide SMEs with consulting or more assistance in the successful adoption of BDSLCCI to secure their cyberspace.
Below is the sample illustration of BDSLCCI certificate awarded to the organization after successful assessment.
Below is the sample illustration of BDSLCCI trascript shared with the organization after successful assessment.
Below is the sample illustration of BDSLCCI controls implementation effectiveness online analytics report shared with the organization after successful assessment.
How Can BDSLCCI Help Organizations Comply with India’s DPDP?
BDSLCCI is well mapped with the DPDP kind of data privacy act requirement. Along with DPDP and other data privacy act policy deployment, BDSLCCI will also allow your organization to:
-
Gap analysis before actual implementation of BDSLCCI recommneded controls
-
Increase visibility across your organization's supply chain
-
Implement your organization's vendor risk assessment process by adopting BDSLCCI and recommending vendors to adopt the similar
-
Generate instant web analytics report showing coverage and effectiveness of the controls implementation
-
Stayed informed on relevant data breaches and industry information via cyber alert email notifications
-
Monitor all endpoint risks in one centralized dashboard by using SecureClaw Crawler tools
-
Cybersecurity awareness online training for each employee
-
Access to key cybersecuirty policy documentation for your organization
-
Cybersecurity awareness posters and banners for spreading best practices for employees
-
Organizations that process personal data can also utilize BDSLCCI cybersecurity framework to be more cybersecure
Conclusion
To sum up, because of the economic and geopolitical ramifications, cybersecurity has emerged as a crucial facet of world affairs that need proper attention. Given the limited success of efforts to establish a rules-based order in cyberspace, it is time for cybersecurity to play a larger role to fulfill requirement of the Digital Personal Data Protection (DPDP) in India. As 90% of businesses worldwide are small and medium companies, BDSLCCI kind of cybersecurity frameworks can easily be adopted and can contribute in maximum impact.