What is Phishing Attack?
Email, or electronic mail, is a communication technique that sends messages via electronic devices across computer networks. The term "email" can apply to both the method of delivery and the specific messages that are sent and received.
Since Ray Tomlinson, a programmer, invented a mechanism to send messages between computers on the Advanced Research Projects Agency Network (ARPANET) in the 1970s, email has existed in some form With the introduction of email client software (like Outlook) and web browsers, which allow users to send and receive messages via web-based email clients, modern versions of email have been widely accessible to the general public (e.g. Gmail, Yahoo Mail, Hotmail).
One of the most widely used digital communication channels nowadays is email. Due to its widespread use and security flaws, it is also a popular target for online threats such domain spoofing, phishing, and business email compromise (BEC). Emails are more likely to be intercepted, and hackers may exploit them to discover covert communications. Viruses, threats, and scams that can lead to the loss of data, personal information, and even identity theft are routinely included in emails. Therefore, it is crucial to find and remove people and devices that are abusing email services. In order to gather reliable evidence to prosecute criminals, email forensic analysis is used to examine the origin and content of email messages as evidence, identifying the real sender, receiver, date and time it was received, etc.
HR department receives a large number of resumes via email, and finance department receives invoices. In most organizations, HR and finance departments are easy targets for hackers, and phishing attacks generally target their email addresses.
by Dr. Shekhar Pawar
Table of Contents
How does Email work?
Mail User Agent (MUA)
Mail Submission Agent (MSA)
Mail Transfer Agent (MTA)
Mail Delivery Agent (MDA)
Protocols Used in The Electronic Mail System
Phishing Attacks Use Victim Psychology
General Tips to Identify Phishing Attacks
Recommended Best Practices to Avoid Phishing Attacks
Trace an email with its full headers
How to read email full headers?
Phishing Email Analysis Methods
How does Email work?
Please see the image below, which depicts an email exchange between sender John and recipient Stella using the email addresses j@grassdew.com and s@secureclaw.com, to see how email delivery works.
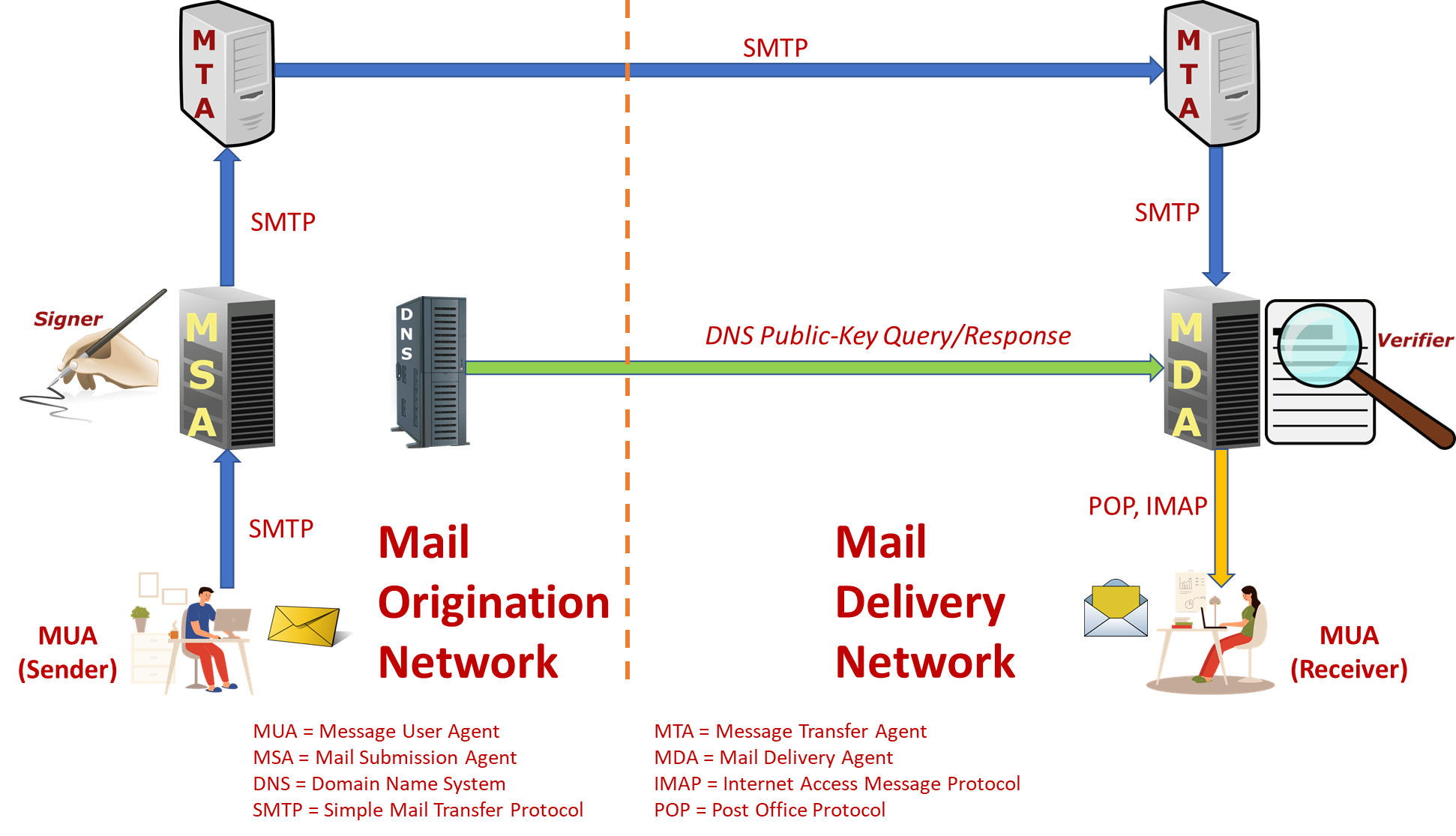
- Using the SMTP protocol, John (j@grassdew.com) creates an email for Stella (s@secureclaw.com) on his computer and sends it to his sending SMTP server (smtp.secureclaw.com).
- The Domain Name System (DNS) protocol on the DNS server dns.grassdew.com is used by the sender SMTP server to conduct a lookup to locate the mail exchange record of the receiving server grassdew.com.
- The highest priority mail exchange server for the domain mx.grassdew.com is returned by the DNS server which is grassdew.com.
- The email message will be sent from the sending server to the receiving server over an SMTP connection, where it will be delivered to Stella's mailbox.
- Stella uses the POP3 or IMAP protocols to download the email from her mailbox on the receiving server to a local mailbox (such as Mozilla Thunderbird) on her client computer, or she may access webmail (through a web browser) to read the email directly on the receiving server.
In order to guarantee interoperability between its users and among the components along the course of transfer, the Email system integrates a number of hardware and software, services, and protocols.
Mail User Agent (MUA)
A computer application or piece of software called a Mail/Message User Agent (sometimes called an email client) enables the User Actor to send and receive emails. It is referred to as the Receiver Mail User Agent (RMUA) on the recipient side and the Author MUA (aMUA) on the sender side (rMUA). Initial submission is carried out by aMUA using Mail Submission Agent (MSA). Additionally, it has the ability to archive message creation and publishing times in its message store.
Receiving mail is processed by rMUA, which also creates user-level disposition control messages, displays and discards the message, and initiates responses and forwards new messages to close or widen the user communication loop. A Mediator is a unique MUA since they carry out message re-posting. MUA can be automated for bulk emailing services and automatic responders (providing out-of-office notices). MUA-relevant identification fields include From, Reply-To, Sender, To, CC, and BCC.
Client computer software programs known as Mail User Agent (MUA) nodes enable end users to compose, create, and read email. Email can be sent directly or indirectly to recipient MTAs using some MUAs.
Microsoft Outlook, KDE KMail, Apple Mail, Microsoft Outlook Express, Lotus Notes, Netscape Communicator, Qualcomm Eudora, and Mozilla Thunderbird are a few examples of mail user agents (MUAs). MUAs are also used with a number of Webmail services and applications, including AIM Mail, Yahoo Mail, Gmail, and Hotmail, which combine e-mail clients and servers behind a Web server.
Mail Submission Agent (MSA)
A Mail/Message Submission Agent (MSA) is a computer program or software agent that works with the Mail Transfer Agent (MTA) to deliver mail once it has been received from a Mail User Agent (MUA). It employs ESMTP, an RFC 6409-specified variation of the Simple Mail Transfer Protocol (SMTP).
It agrees to post the message that the aMUA has supplied. Before publishing the message from an Authors environment to the MHS, it enforces the hosting ADMD's regulations and the needs of Internet standards. These include extending an address to its official Internet Mail Format (IMF) representation and adding header information like Date and Message-ID. Transiting the message to the MTA is the responsibility of the MHS-focused Mail Submission Agent (hMSA). The identification fields HELO/EHLO, ENVID, MailFrom, RcptTo, Received, and SourceAddr are pertinent to the MSA. One Agent may have both the MUA's and the MSA's obligations. Although the MSA's official port is 587, MTA and MSA agents have historically both used port number 25.
Mail Transfer Agent (MTA)
Mail is relayed through a Mail/Message Transfer Agent (MTA) for one application-level "hop". For each email to be sent, MTA nodes, which are essentially postal sorting agents, are responsible for getting the pertinent Mail eXchange (MX) record from the DNS Server. This allows them to associate the individual e-mail addressee's domain name with the pertinent IP address information. The DNS is a distributed directory database that links IP addresses to domain names. Email message creation and composition are both possible with MTAs. Sendmail, Postfix, Exim, and Exchange Server are a few MTAs. A receiving MTA is also known as a mail delivery agent since it is capable of carrying out the task of delivering an email message to the recipient's specific mailbox on the mail server (MDA).
MTAs are supposed to retain messages in a way that enables recovery despite service disruptions such host-system shutdown, in contrast to conventional packet switches (and Instant Messaging systems). MTAs can give varying levels of sturdiness and tenacity. An MTA can take on the well-defined responsibilities of Final MTAs or Boundary MTAs (Onbound or Inbound). The identification fields HELO/EHLO, ENVID, MailFrom, RcptTo, Received, and SourceAddr are pertinent to MTAs.
Mail Delivery Agent (MDA)
A Mail/Message Delivery Agent (MDA) is a computer program that receives email from a Mail Transfer Agent (MTA), sorts the email, and then delivers it to the recipient's inbox. The message must be accepted for delivery to separate addresses by both the MHS-focused MDA (hMDA) and Receiver-focused MDA (rMDA).
The rMDA handles the delivery activity while the hMDA serves as an SMTP server engine. Return-Path and Received are the identity fields that are pertinent to MDA.
Protocols Used in The Electronic Mail System
The email nodes connect to one or more nodes on specified ports in order to potentially exchange email using a particular protocol. SMTP is an application layer protocol for TCP/IP-based Internet infrastructure that establishes grammatical and conversational conventions for computer-to-computer email communication. Post Office Protocol Version 3 (POP3) and Internet Message Access Protocol are the most widely used protocols for e-mail retrieval by client applications (IMAP).
The numerous protocols and corresponding port numbers are shown in the table below.
| Port Number |
Protocols/Services |
Description |
| 25 |
SMTP, SMTP e-mail server
|
Simple Mail Transfer Protocol - core Internet protocol used to transfer from client to server (MUA to MTA) and server to server (MTA to MTA) |
| 80 |
HTTP |
Webmail |
| 110 |
POP3, POP e-maiI server |
Post Office Protocol allowsclients (MUA's) to retrieve stored e-mail |
| 143 |
IMAP, IMAP(4) e-mail server |
Internet Message Access Protocol provides a means of managing e-mail messages on a remote server and retrieve stored e-mail |
| 443 |
HTTPS |
Secure Webmail |
| 465 |
SMTPS, WSMTP (SSMTP) protocol over TLS/SSL |
SMTP via SSL encrypted connection (Unofficial) |
| 587 |
MSA |
Outgoing Mail (Submission) |
| 993 |
IMAPS, SSL encrypted IMAP |
IMAP via SSL encrypted connection |
| 995 |
POP3S SPOP, SSL encrypted POP |
POP via SSL encrypted connection |
Generally, incoming emails are handled by POP3 and IMAP, and each of them has a unique manner of retrieving or accessing your email messages. They are regarded as mail access protocols as a result. On the other hand, the message transport from mail client to server is handled via the Simple Mail Transfer Protocol. This protocol is known as the outgoing protocol since it manages email sending from an email account. In essence, you can receive emails owing to IMAP and POP3, and you may send messages thanks to SMTP.
Phishing Attacks Use Victim Psychology
Phishing emails, on the other hand, usually share traits; they are frequently written to arouse emotions like curiosity, pity, fear, and greed. The time spent teaching a workforce to recognize a phishing email can stop assaults and network infiltration by the attacker if they are informed of these features and taught what to do when a danger is anticipated.
-
Emails requesting immediate action
Phishing emails frequently contain threats of unpleasant outcomes or missed opportunities unless immediate action is taken. Attackers frequently employ this strategy to pressure recipients into taking action before they have had a chance to carefully read the email for any potential errors or inconsistencies.
-
Unfamiliar Greetings or Salutations in Emails
Typically, emails sent and received between coworkers begin with a casual greeting. Those that begin "Dear" or contain words that aren't often used in casual conversation are coming from people who aren't familiar with the manner of workplace communication in your company and should raise concern.
-
Emails asking for payment information, sensitive data, or login credentials
Always exercise caution when responding to emails that require login credentials, financial information, or other sensitive data from an unexpected or unfamiliar source. Spear phishers can create phony login sites that resemble the genuine article and then send an email with a link that takes the receiver to the false page. When a receiver is sent to a login page or informed that a payment is required, they should not enter any information unless they are positive the email is authentic.
-
Emails that seem too good to be true
In emails that seem too good to be true, the sender entices the receiver to open an attachment or click on a link by promising a prize of some sort. It's likely a phishing email if the sender of the email is unknown or if the receiver does not initiate contact.
General Tips to Identify Phishing Attacks
Due to their intelligence, socially engineered phishing emails frequently escape email filters. They are seldom transmitted in bulk from blacklisted IP addresses to avoid being banned by Realtime Blackhole Lists, have the proper Sender Policy Frameworks and SMTP restrictions, and pass the filter's front-end checks. They can even elude detection from sophisticated email filters with Grey-listing capabilities because they are frequently uniquely created.
-
Emails with errors in grammar and spelling
Grammar and spelling errors are another sign of phishing. Many businesses automatically spell-check outgoing emails to make sure they are grammatically accurate. Users of browser-based email clients employ web browser autocorrect or highlight functions.
-
Consistency issues with domain names, links, and email addresses
Finding irregularities in email addresses, URLs, and domain names is another approach to recognize phishing. Does the sender of the email regularly contact with that company? If so, compare the sender's address to those on earlier emails from the same company. Hover the mouse pointer over a link to see what appears to determine whether it is real. Report the email as a phishing assault if it purports to be from (let's say) Google but the domain name says something else.
-
Unusual Attachments
Collaboration solutions like SharePoint, OneDrive, or Dropbox are currently used for the majority of file sharing linked to work. Internal emails with attachments should thus always be viewed with suspicion, especially if they have an unknown.
Recommended Best Practices to Avoid Phishing Attacks
Here are 11 quick guidelines for spotting and avoiding phishing schemes.
-
Know how to spot phishing scams
Although new phishing attack techniques are always being created, they all have some characteristics that may be seen if you know what to look for. There are several websites online that can keep you up to date on the most recent phishing assaults and their distinctive characteristics. The more frequently you do security awareness training for your users and the earlier you learn about the most recent attack techniques, the more likely you are to prevent a prospective assault.
-
Beware of Short Urls
If you have long web url, you can shorten it using various websites like https://bitly.com/
For example, here is one of the short url.
You may reduce large web addresses utilizing a variety of websites, including : https://bitly.com/
As an illustration, here is a short url we made : https://bit.ly/2RQULYs
It really goes to a lengthy url : https://grassdew.com/Leadership
It is quite difficult to predict where a short url will travel in this situation when someone receives it and clicks on it. Who knows if it will be a phishing assault or a cyber trick that directs users to a bogus website?
You may use the websites listed below to determine the long url for your short url.
-
Avoid clicking that link
Even if you know the sender, it's typically not a good idea to click on a link in an email or instant message. You should at the very least be lingering over the link to check that the destination is the right one. The destination URL of certain phishing attempts might resemble an exact replica of the legitimate website and be designed to capture keystrokes or collect login and credit card information. You should bypass the link and go directly to the website if it's feasible to do so using your search engine.
-
Install anti-phishing extensions
Nowadays, the majority of browsers allow you to download add-ons that detect the telltale characteristics of a fraudulent website or warn you about well-known phishing websites. There is no reason not to have this installed on every device in your company as they are often entirely free.
-
Avoid providing your information to unsafe websites
Don't enter sensitive information or download files from a website if the URL doesn't begin with "https" or if you can't see a closed padlock icon next to the URL. It's possible that phishing schemes are not designed for websites lacking security certifications, but it's better to be safe than sorry.
-
Change passwords frequently
If you have any online accounts, you should make it a practice to change your passwords often in order to stop an attacker from acquiring unrestricted access. By adding an extra layer of security through password rotation, you may stop ongoing assaults and keep potential attackers out of your accounts even if you weren't aware that your accounts had been hijacked.
-
Take note of those updates
It might be annoying to constantly get update alerts, and it can be tempting to delay or disregard them. Avoid doing this. Security updates and patches are published for a cause, most frequently to close security gaps in order to stay current with contemporary cyber-attack techniques. If you don't upgrade your browser, you can be vulnerable to phishing attempts that might have been easily prevented by taking use of known flaws.
-
Put up firewalls
Firewalls serve as a barrier between your computer and an attacker, thereby preventing external attacks. When used in tandem, desktop and network firewalls can increase security and lessen the likelihood that a hacker will infiltrate your environment.
-
Avoid being seduced by those pop-ups
Pop-ups aren't simply annoying; they're frequently connected to malware as a result of phishing attempts. You may now download and install free ad-blocker software that will automatically prevent the majority of dangerous pop-ups from most browsers. But if one manages to get past the ad-blocker, resist the urge to click! Sometimes pop-ups will try to trick you by hiding the "Close" button in a different location, so always try to search for a "x" in the corner.
-
Don't divulge sensitive information until absolutely necessary
As a general guideline, you shouldn't readily give up your card information unless you completely trust the website you are visiting. If you must disclose your information, be sure to confirm the legitimacy of the website, the legitimacy of the company, and the security of the website.
-
Have a Data Security Platform to spot signs of an attack
It's critical that you can recognize and respond quickly to phishing attacks in case you are unlucky enough to fall prey to one. By automatically warning on unusual user activity and unauthorized file modifications, a data security platform relieves some of the load on the IT/Security team. If an attacker has access to your sensitive information, data security platforms can help to identify the affected account so that you can take action to prevent further damage.
Trace an email with its full headers
Different email provider have different methods to trace email header.
How to examine header of Gmail
From a browser, open Gmail.
-
Open the email you want to check the headers for.
-
Next to Reply icon, click More (three verticle dots) and then Show original.
-
The headers will show in a new window, including fields like authentication results. To get the full message header, click Download original.
How to examine header of AOL
-
Log in to your AOL account.
-
Open the email you want to see the headers for.
-
In the "Action" menu, select View Message Source.
The headers will show in a new window.
How to examine header in Hotmail
-
Log in to your Hotmail account and click on Inbox.
-
Right-click the email you want to see the headers for.
-
Click View Message Source.
The headers will show in a new window.
How to examine header in Excite Webmail
-
Log in to your Excite account.
-
Open the email you want to see the headers for.
-
Click View Full Headers.
The headers will show in a new window.
How to examine header in Yahoo! Mail
-
Log in to your Yahoo! Mail account.
-
Select the email you want to see the headers for.
-
Click More and then View Raw Message.
The headers will show in a new window.
How to examine header in Apple Mail
-
Open Apple Mail.
-
Open the email you want to see the headers for.
-
Click View and then Message and then All Headers.
The headers will show in the window below your inbox.
How to examine header in Mozilla.
-
Open Mozilla.
-
Open the email you want to see the headers for.
-
Click View and then Message Source.
The headers will show in a new window.
How to examine header in Opera.
-
Open Opera.
-
Click the email you want to see the headers for so it shows in the window below your inbox.
-
Right click the body of the email.
-
Click View All Headers and Message.
The headers will show in the window below.
How to examine header in Outlook.
-
Open Outlook.
-
Open the email you want to see the headers for.
-
Click File and then Properties.
The headers will show in the "Internet headers" box.
How to examine header in Outlook Express.
-
Open Outlook Express.
-
Right click the email you want to see the headers for.
-
Click Properties.
-
Click the Details tab.
The headers will show in the box that pops up.
How to read email full headers?
Copy the text on the page.
Open the Google Message Header Tool.
In "Paste email header here," paste your header.
Click Analyze the header above.
Phishing Email Analysis Methods
There are many different ways to conduct an investigation into incidents and crimes using email, employing a variety of techniques. A discussion of them is given below:
Examining Email Headers
Email header analysis is the primary analytical technique. To do this, email header metadata analysis is necessary. By looking through header information, it is possible to identify the majority of email-related crimes. You can identify email spoofing, phishing, spam, fraud, and even internal data leaks by looking at the header.
It is crucial that we acquire the complete message headers from a message when reporting spam that manages to bypass the filters. Additionally, in order to diagnose mail delivery issues, our Support staff may occasionally ask for the whole headers from an email message.
The header and the message body are the two components that make up each and every Internet email message. A complete and legitimate email header offers a thorough account of the network route that the message took between the mail sender and the mail receiver(s) in every email you send or receive on the Internet (email servers).
Typically, your email client software will either conceal the entire header or simply show lines like From, To, Date, and Subject.
Below is one of the example of spam email.
You can view message headers in Outlook on your desktop.
1. Double-click an email message to open it outside of the Reading Pane.
2. Click File > Properties.
3. Header information appears in the Internet headers box.
Tip: You can highlight the information in that box, press Ctrl+C to copy, and paste it into Notepad or Word to see the entire header at once.
Below is a snapshot of the email header. Note that, "Return-Path" is different than "Reply-To".
While using this method, the forensic investigator should pay particular attention to the following.
-
Make that the "From:" and "Return-Path:" fields are same.
-
Make sure the "Reply-To:" and "From:" fields are identical.
-
Bulky X-distribution can be used to identify spam.
-
Examining an email's X-spam score and flag can reveal whether it is spam.
Digital forensic experts utilize this information in their email investigation to identify scammers.
Investigating the Server
Server inquiry involves looking through email copies and records kept on the mailing server to ascertain a message's source. If the sender or receiver of the email has deleted it, investigators resort to the Internet Service Provider (ISP) or proxy servers to find a stored copy of the email. A proxy server acts as a bridge between the end user and the website domain.
The ability to identify a person is further aided by SMTP servers that retain information on the mailbox owner, such as a credit card number. However, this sort of analysis typically proves to be resource-intensive since it requires substantial processing to retrieve any important information and takes time because logs and backup emails must be received from the proxy server or the ISP (some may not cooperate with the investigators). Additionally, server logs and email copies are only stored for a limited period of time (which vary according to the applicable legislation).
As soon as possible, the investigator needs to review the server logs in the receiving chain. Since HTTP and SMTP data are frequently retained, especially by big ISPs, punctuality is critical in email scenarios. It could be challenging and time-consuming to find and decompress the log files needed to find emails if a log is preserved.
If server investigation is not an option, investigators may turn to network device investigation, a famously challenging type of research that requires looking through the logs kept by network devices like switches, routers, and firewalls.
Network Device Analysis
On rare occasions, the aforementioned logs are unavailable. This can be due to ISPs' lack of setup or unwillingness to transmit log files. In this case, forensic cyber experts search for evidence in the data saved by switches and routers and other network hardware.
Bait Techniques
As part of a bait strategy investigation, an email with an image source from a computer being observed by the investigators and a real (genuine) email address is sent to the sender of the email being investigated. When an email is read, the IP address of the recipient (the sender of the email under investigation) is recorded in a log entry, enabling sender tracking on the http server hosting the image. If the recipient (sender of the email in question) is doing this, the IP address of the proxy server is notated. The log on function of the proxy server can be used to locate the sender of the email under investigation. If the proxy server's log is unavailable for whatever reason, investigators may utilize the technique of sending an email with an embedded Java applet that runs on the recipient's PC or an HTML page with an Active X object. both attempting to send the IP address of the recipient's machine to the investigators.
Identifiers Embedded in Software
Examining software embedded identifiers is another investigative technique to learn more about the sender or the content of the message (such as attached files) through information incorporated by the email client or software used by the sender. Common forms for this data include custom headers or MIME (Multipurpose Internet Mail Extensions) content. Even while this kind of research takes a lot of time, it might provide important details about the sender's email preferences and settings, which could aid in obtaining client-side evidence.
This information might be sent using specific headers or as MIME content with a transport-neutral encapsulation style (TNEF). To facilitate the transmission of single texts, numerous texts, and non-text attachments, the MIME internet standard has been established. Microsoft Outlook and Microsoft Exchange Server employ an exclusive and unshared email attachment format known as TNEF.
Research can reveal PST file names, Windows logon identities, MAC addresses, and other details about the client system used to send email. Similar to how email handling software at the sender's end and received header information may reveal the server's email management software (due to the different structure in headers). This analysis is a phase of a procedure known as sender mailer fingerprinting, which may characterize client-side programs and their versions in addition to disseminating characteristics and weaknesses of the host machine that the client application is executing on.
Message Sender Fingerprints
In addition to the "subject," "from," and "to" headers, emails also contain X-headers. Experts that follow this data check for the IP address of the transmitting device.
During the study of an email, the sender mailer fingerprinting approach finds the sender's software and its version. Examples include Gmail, Outlook, Hotmail, and others. This information about the sender's client computer may be used to assist investigators develop a successful plan, which makes it very useful.
Employing Email Trackers
Attackers have been known to create emails utilizing a number of tactics and locations. In such cases, the attacker's position has to be determined. To find the perpetrator's actual location, investigators typically use email tracking software that is included in an email body. When a receiver opens an email that has an email tracker attached, the investigator will receive a notification containing the recipient's IP address and location. This method of identifying suspects in murder or kidnapping cases is typically used when a criminal utilizes email to communicate.
Analyzing Email Attachments
Email attachments are the primary method of malware and virus transmission. Investigating the attachments is crucial in any email-related investigation. The leaking of private information is a key topic of research. Email-related data, including attachments, may be recovered from computer hard drives using software tools. In order to examine suspicious attachments and establish whether or not the file includes malware, investigators can submit files to an online sandbox like VirusTotal. It is important to remember that just because a file passes a test like VirusTotal's doesn't mean it is 100 percent secure. If this happens, it is advised to further examine the file in a sandbox environment using a program like Cuckoo.
Every business domain has unique mission critical assets and different cybersecurity needs.
We partner for your entire journey of cybersecurity implementation. Business Domain Specific Least Cybersecurity Controls Implementation (BDSLCCI) framework and certification is the solution for cost-effective cybersecurity implementation. Click Here To Know More About BDSLCCI Certification!